Wednesday, October 7, 2009
Build a website - easily
? Articles that convey exactly what you are trying to say about a software product or development? Or are you simply a consumer who is looking for an extra bit of guidance or advice when it comes to what Computer Software does and what is the best Computer Software for you to buy for your needs?
If any of these things describe what you are currently looking for then you have certainly come to the right place. This Computer Software section here at Article Alley aims to help people in all of the above situations and much more. This is thanks to all of the articles that are submitted to us on a daily basis from all of our dedicated authors. All of the articles relevant to aspects of Computer Software are then placed into this section ready for you to use in whatever way you need to.
Saturday, September 26, 2009
How can i copy the files in the debug folder to some other directory automatically ?
Add the following line of code to the Post build event in the project properties,
call copy E:\projectdir\bin\Debug c:\test\
What is the name of the file you need to change to add pre- and post-build functionality into your custom package ?
Targets file.
It is located in ,
%WINDOWS%\Microsoft.NET\Framework\v2.0.50727\Microsoft.Common.targets
Tell some of the new features of ASP.NET 3.5?
1. Expression Trees
2. Controls
1. ListView
2. DataPager
3. Support for LINQ, WCF , WPF and WWF
What are the options available on creating a branch?
There are 5 options available on creating a branch, they are :
1. Changeset
2. Date
3. Label
4. Latest Version
5. Workspace version
How will you check whether automated build is successful and call a custom task on successful build?
You can do that by providing the following config entry in the MS Build or TFS Build config file,
Condition=" '$(IsDesktopBuild)' != 'true' ">
What are the new Features in Team Build 2008 ?
1. Continuous Integration
2. Build Queuing
3. Scheduled Builds
4. Build Agent Management
5. Build Definition Editing GUI
6. Better Build Management
7. Managed object model
8. Improved extensibility
What are the blocks in Enterprise Library?
1. The Caching Application Block
2. The Cryptography Application Block
3. The Data Access Application Block
4. The Exception Handling Application Block
5. The Logging Application Block
6. The Policy Injection Application Block
7. The Security Application Block
8. The Unity Application Block
9. The Validation Application Block
What are the Predefined bindings in WCF?
1. BasicHttpBinding
2. WSHttpBinding
3. WSDualHttpBinding
4. NetTcpBinding
5. NetNamedPipeBinding
6. NetMsmqBinding
What will the deployment retail="true" do when set in a asp.net web.config file?
It forces the 'debug' attribute in the web.config to false, disables page output tracing, and forces the custom error page to be shown to remote users rather than the actual exception.
What is the Svcutil.exe ?
Service Model Metadata Utility Tool is used to generate the proxy from the client.
What are the uses of Views?
of data by joining tables. So you are not storing redundant data.
2. Views are used to produce reports from data
3. Views can be used to provide security to data by giving access only to views.
What’s the difference between authentication and authorization?
Is a process by which the system decides whether the user is valid to login to the site as a whole.
what is Authorization?
Is a process by which the system decides which are the areas and functionalities the user is allowed to access, at the component level.
What is Serialization ? What are the Types of Serialization and their differences?
It is the process of converting an object to a form suitable for either making it persistent or tranportable.
Deserialization is the reverse of this and it converts the object from the serialized state to its original state.
Types:
1. Binary
2. XML
Differences:
| Sno | Binary | XML |
| 1 | It preserves type fidelity , which is useful for preserving the state of the object between transportation and invocation. | It doesnt preserves type fidelity and hence state cant be maintained. |
| 2 | As it is the open standard its widely used | Not that much compared to Binary. |
What is assemblyInfo.cs file? Where can I find it? What is it for?
It consists of all build options for the project,including verison,company name,etc.
Where
It is located in the Properties folder.
Use
It is used to manage the build settings.
What is the name of the class used to read and get details of the files uploaded to asp.net?
What is web.config.? How many web.config files can be allowed to use in an application?
The Web.Config file is the configuration file for
asp.net web application or a web site. prefix="o" ?>
2.
You can have as many Web.Config files as you want
, but there can be only one web.config file in a single folder.
What are asynchronous callbacks in .net?
How to download webpage using asp.net and c# ?
using System;
using System.Collections.Generic;
using System.Text;
using System.IO;
using System.Net;
namespace DownloadingFile
{
class Program
{
static void Main(string[] args)
{
WebRequest reqFile = WebRequest.Create("http://www.codecollege.net/2009/07/cloud-computing.html");
WebResponse resFile = reqFile.GetResponse();
Stream smFile = resFile.GetResponseStream();
// Output the downloaded stream to the console
StreamReader sr = new StreamReader(smFile);
string line;
while ((line = sr.ReadLine()) != null)
Console.WriteLine(line);
Console.Read();
}
}
}
How to download webpage using asp.net and c# ?
using System;
using System.Collections.Generic;
using System.Text;
using System.IO;
using System.Net;
namespace DownloadingFile
{
class Program
{
static void Main(string[] args)
{
WebRequest reqFile = WebRequest.Create("http://www.codecollege.net/2009/07/cloud-computing.html");
WebResponse resFile = reqFile.GetResponse();
Stream smFile = resFile.GetResponseStream();
// Output the downloaded stream to the console
StreamReader sr = new StreamReader(smFile);
string line;
while ((line = sr.ReadLine()) != null)
Console.WriteLine(line);
Console.Read();
}
}
}
How to read and write from a text file using c#.net ?
using System;
using System.Collections.Generic;
using System.Text;
using System.IO;
namespace ReadWriteFromTxt
{
class Program
{
static void readFile()
{
FileStream fsEmp = new FileStream("c:\\Emp.html", FileMode.Open, FileAccess.Read);
StreamReader srEmp = new StreamReader(fsEmp);
string s;
while ((s = srEmp.ReadLine()) != null)
{
Console.WriteLine(s);
Console.Read();
}
srEmp.Close();
fsEmp.Close();
}
static void writeFile()
{
FileStream fsEmp = new FileStream("c:\\Emp.html", FileMode.Open, FileAccess.Write );
StreamWriter swEmp = new StreamWriter(fsEmp );
string s="Have you seen god? Is there anything else to see";
swEmp.WriteLine(s);
swEmp.Close();
fsEmp.Close();
}
static void Main(string[] args)
{
writeFile();
readFile();
}
}
}
what are the Differences between Abstract Class and Interface ?
| Sno | Abstract Class | Interface |
| 1 | Can have implemented Methods | Cant |
| 2 | A class can inherit only one abstract class | A Class can implement any number of Interfaces. |
| 3 | We go for Abstract classes on such situations where we need to give common functionality for group of related classes | We go for Interface on such situations where we need to give common functionality for group of un-related classes |
| 4 | If you add a new method, then you can provide a default implementation and so no need to make any change to existing work. | If you add a new method, then you need to change all the existing work. |
| 5 | Static and Instance constants are possible. | Only Static constants are possible. |
How can you tell the application to look for assemblies at the locations other than its installed location?
How to read and write from a text file using c#.net ?
using System;
using System.Collections.Generic;
using System.Text;
using System.IO;
namespace ReadWriteFromTxt
{
class Program
{
static void readFile()
{
FileStream fsEmp = new FileStream("c:\\Emp.html", FileMode.Open, FileAccess.Read);
StreamReader srEmp = new StreamReader(fsEmp);
string s;
while ((s = srEmp.ReadLine()) != null)
{
Console.WriteLine(s);
Console.Read();
}
srEmp.Close();
fsEmp.Close();
}
static void writeFile()
{
FileStream fsEmp = new FileStream("c:\\Emp.html", FileMode.Open, FileAccess.Write );
StreamWriter swEmp = new StreamWriter(fsEmp );
string s="Have you seen god? Is there anything else to see";
swEmp.WriteLine(s);
swEmp.Close();
fsEmp.Close();
}
static void Main(string[] args)
{
writeFile();
readFile();
}
}
}
Sunday, June 21, 2009
Microsoft Office 2010 (Portable)

Microsoft Office 2010 or Office 14 - the working title of the next version of Microsoft Office for Microsoft Windows. Microsoft started work on Office 2010 in 2006, which ended the work on the Microsoft Office 12 (which went under the name of Microsoft Office 2007).
Includes:
Word 2010, Excel 2010, PowerPoint 2010
Initially it was thought that Office 2010 will be released for sale in the first half of 2009, but the new data it is not expected before late 2009 and early 2010. It is anticipated that Office 2010 will be presented at about the same time with the new operating system Microsoft Windows 7. According to an article in InfoWorld in April 2006, Office 2010 will be a «role», than previous versions. The article quoted Simon Vittsa (eng. Simon Witts), vice-president of Microsoft's Enterprise and Partner Group, which said that the package will focus on some of the staff - researchers, developers, managers, HR. Office 2010 borrows some ideas from the ideology of «Web 2.0», and, perhaps, Microsoft SharePoint Server to build capabilities in new version of office suite.
Office 2010 implements the ISO version is compatible with Office Open XML, which has been standardized as ISO 29500 in March 2008. Microsoft also plans to provide Web-version of its Office products, known as Office Web, debuted along with Office 2010. Office Web will include online versions of Word, Excel, PowerPoint and OneNote. It was expected that the new version will be distributed free of charge, but revenues will be removed from advertising. In addition, Office 2010 will be offered in two versions - to 32-bit and 64-bit processors. Microsoft Office 2010 Technical preview will be released in late June - early July. Send it can be only by invitation. But you can apply now. However, Microsoft Office 2010 Technical Preview is already safely land in the network.
Brought to you by Agroni112
Thanks!
Download:
http://rapidshare.com/files/245540079/_www.dl4all.com_O.2010_Portable_ag112.part2.rar
http://rapidshare.com/files/245539213/_www.dl4all.com_O.2010_Portable_ag112.part3.rar
Password: www.dl4all.com
Hiren's BootCD 9.9 With Multilingual Keyboard Patch

Hiren's Boot CD is a boot CD containing various diagnostic programs such as partitioning agents, system performance benchmarks, disk cloning and imaging tools, data recovery tools, MBR tools, BIOS tools, and many others for fixing various computer problems. It is a Bootable CD; thus, it can be useful even if the primary operating system cannot be booted. Hiren's Boot CD has an extensive list of software. Utilities with similar functionality on the CD are grouped together and seem redundant; however, they present choices through UI's differences and options in what they can do.
Hiren's BootCD - All in one Dos Bootable CD which has all these utilities:: Partition Tools, Disk Clone Tools, Antivirus Tools, Recovery Tools, Testing Tools, Hard Disk Tools etc.
Hiren's BootCD 9.9
+SuperAntispyware 4.26
-Ad-Aware SE Personal
+EASEUS Partition Master 3.5
+Video Memory Stress Test 1.7.116
+MessenPass 1.24
+Mail PassView 1.51
+Asterisk Logger 1.04
+TrueCrypt 6.2
+Opera Web Browser 8.53
-Off By One Browser
-Aida16 2.14
+Kaspersky Virus Removal Tool 7.0.0.290
-ClamWin Antivirus
+Registry Restore Wizard 1.0.4
HDD Regenerator 1.61
SPecial FDisk 2000.03v
Express Burn 4.26
TestDisk 6.11.3
PhotoRec 6.11.3
Recuva 1.27.419
IsMyLcdOK (Monitor Test) 1.01
Samsung The Drive Diagnostic Utility (ESTOOL) 2.12a
IBM/Hitachi Feature Tool 2.13
System Analyser 5.3v
Astra 5.42
HWiNFO 5.2.7
SIW 2009-05-12
CPU-Z 1.51
WirelessKeyView 1.26
CCleaner 2.20.920
CurrPorts 1.65
Autoruns 9.50
Ultimate Windows Tweaker 1.2
Xp-AntiSpy 3.97.3
Shell Extensions Manager (ShellExView) 1.37
Malwarebytes' Anti-Malware 1.37 (0906)
SpywareBlaster 4.2 (0906)
SmitFraudFix 2.419
ComboFix (0906)
Spybot - Search & Destroy 1.6.2 (0906)
PCI 32 Sniffer 1.4 (0906)
PCI and AGP info Tool (0906)
Unknown Devices 1.2 (0906)
www.hiren.info/bootcd
ISO MD5: 9b797871bab60ebe80363a26d167b0a4
Download Links
Saturday, June 20, 2009
Exchange Server Database Corruption Due to “Error 1067”
One such scenario occurs when you try to start directory server in Exchange Server after restoring from backup. When you try to do this, you may encounter the following error message:
“Error 1067. The process terminated unexpectedly.”
Along with this error message, the following event entries might appear in the Application Even Log:
Event ID: 124
Source: ESE97
Description: MSExchangeDS ((1432 ) ) Unable to read the log header.
Error -530.
Event ID: 1196
Source: MSExchangeDS
Description: Couldn’t recover the restored Microsoft Exchange Server
database (EDB). Cannot continue. Error c8000212.
After this error message, you can not access anything from your Exchange Server database and may fall in need of Exchange Server recovery.
Reason of this issue
This problem generally occurs when Edb.log file, which is created while performing restoration from backup, interfaces with recovery process. It occurs on recovery server.
Due to this problem, the recovery process could not be completed successfully and you might face this behavior of Exchange Server. It cause complete inaccessibility of Exchange Server database.
Work around
To fix this problem, manually delete the existing data from the Dsadata folder before starting restore operation from the backup. It will delete Edb.log file.
Though, it could fix the issue, but it is not a safe method. Deleting Edb.log file might introduce severe errors in the Exchange Server database and may corrupt it.
EDB corruption is the worst scenario for a database user and it might put him/her in need of exchange server repair. Exchange Server repair can easily be carried out using Exchange Server recovery software.
Stellar Phoenix Mailbox Exchange Recovery software is the best ever made Exchange Server repair software to work around all the corruption issues. Using this Exchange Server recovery software, you can perform easy, quick and absolute Exchange Server repair. Phoenix Exchange Server Repair is applicable to all the Exchange Server file versions.
Error -1216 in Exchange Server and EDB Recovery
It is the most common Jet error in Microsoft Exchange Server. Error -1216 shows that the Exchange Server has determined that the files in Exchange Server database’s running set are lost or they have been reinstated with the different file versions.
Error -1216 could also be symbolized hexadecimally as ‘0xfffffb40’. When the error takes place, the Exchange Server aborts the soft recovery of EDB file before doing some changes to database, which may prevent re-integration of missing database files with data set.
When this error takes place, you should attempt to restore the missing database files. When these files are not available, you could use Eseutil for overriding the error and go on with software EDB recovery.
Error -1216 is caused when the comparison of header information in database and the log files shows that the removal or replacement of some critical files has been done. This error message may cause data loss, if the administrator run the soft recovery.
Grounds of the trouble
This problem occurs due to the inconsistency of the database, which might occur due to unexpected shut down of the Exchange Server or the Storage Group service has been stopped improperly. You may find the following entries in the Application Event Log, when the Exchange Server was stopped abnormally:
“Event Type: Error
Event Source: ESE98
Event Category: Logging/Recovery
Event ID: 0
Date: 4/24/2001
Time: 6:20:18 PM
User: N/A
Computer: EXCHANGE1
Description: Information Store (4312) Database recovery failed with error -1216 because it encountered references to a database, ‘D:\exchsrvr\mdbdata\PRIV2.edb’, which is no longer present. The database was not brought to a consistent state before it was removed (or possibly moved or renamed). The database engine will not permit recovery to complete for this instance until the missing database is re-instated. If the database is truly no longer available and no longer required, please contact PSS for further instructions regarding the steps required in order to allow recovery to proceed without this database.
Nevertheless the cause of this issue, the database inconsistency will ultimately cause EDB corruption and finally the data loss. In such circumstances, you need to perform Exchange Server recovery to recover your lost data. It is feasible using good EDB repair software such as Stellar Phoenix Mailbox Exchange Recovery.
Phoenix Exchange Server repair is extremely powerful EDB recovery product to handle EDB corruption scenarios. It can perform Exchange Server recovery for all of the EDB repair objects including emails, notes, contacts and so forth. Phoenix Exchange Server repair is applicable to all file versions of Microsoft Exchange Server including Exchange 5.5, 2000, and 2003.
EDB Corruption When Defragmentation Fails
You could use Eseutil utility for defragmenting the Exchange Server database. It examines the basic structure of the database and rearrange them. It is required for better performance of the database.
Sometimes when you defragment the database, the process fails half-way though. After the process gets halted, you get a temporary file of Priv1.edb. When you rename this file, it gets disappeared. In such situations, the Mailbox store gets corrupted and you can not mount it. In this case, when you use the Eseutil /MS (to dump the space usage), the operation gets terminated with the following error message:
“Error -2211 (JET_errSLVHeaderCorrupted, SLV file header contains invalid
information)”
After getting this corruption error message, when you use Eseutil /P to repair the database, you will get the further error message stating:
“Checking database integrity. Operation terminated with error -1206 (JET_errDatabaseCorrupted, Non database file or corrupted db) after 1.912 seconds.”
This behavior results into the inaccessible Exchange Server database. You can not retrieve even a single bit of data from the database and you may fall in the grave situations of data loss.
Cause
As stated in the above error message, this problem takes place due to damaged Exchange Server database. The database corruption could be the possible result of unexpected system shutdown, virus attack, oversized EDB file and so forth.
It does not matter what the reason of data loss is. The only thing which matter is how to retrieve your precious data? The answer of this question is Exchange Server recovery.
Exchange recovery is the process of repairing the damaged database with the help of EDB recovery software and restore it. EDB recovery software are easy to use tools, which help you in all cases of EDB corruption and can recover all of the EDB objects.
Stellar Phoenix Mailbox Exchange Recovery is the most advanced Exchange Server repair software. It supports EDB repair from Exchange Server 5.5, 2000, and 2003. It systematically scans the entire database and ultimately gives you fruitful results of Exchange Server recovery.
Error While Moving Exchange Server Mailboxes
Using Move Mailbox Wizard, MS Exchange Server allows moving mailboxes within any versions of MS Exchange, MS Exchange Server 5.5, 2000 and 2003, under a condition that they should be within same Exchange organization. But, when the user tries to move mailboxes from Exchange Server 5.5 to Exchange Server 2000, the process may fail with the following error message:
Error: Moving messages
CN=TestUser,CN=Users,
DC=Machine,DC=Company,DC=Com:
The MAPI call failed.
MAPI or an unspecified service provider.
ID no: 80004005-0000-00000000
Viewing Application log of Exchange Server 2000 shows that the application is failing to move some of the mailboxes. The problem is associated with few of the mailboxes which contain corrupt messages, stripped or disassociated attachment. In case of corrupt messages in mailboxes, EDB gets corrupt and needs exchange server recovery. When we click the messages of mailboxes, which contain the disassociated or stripped attachments, some error messages are encountered which states that attachment can’t be opened or access is denied.
* In order to resolve this issue, we need to permanently delete the message using SHIFT+DELETE or simply deleting the message and emptying the Deleted Items folder.
* If corruption is high, we need to repair EDB as a whole using Eseutil utility or EDB Repair software. Eseutil deletes the corrupt pages from corrupt database; however, this is safe to use EDB Recovery software which apply safe, yet powerful scanning algorithms to extract lost information from corrupt database.
Stellar Phoenix Mailbox Exchange Recovery is a powerful EDB Repair application which is compatible with Exchange Server 5.5, 2000 and 2003. This EDB Recovery software has interactive interface and restores recovered mailboxes in PST format, usable with MS Outlook. The application can recover all the database objects.
What is the meaning of 1216 error in Exchange Server and how to recover?
Sometimes this error 1216 shows in hexadecimal like “0xfffffb40”. When the error generates, Exchange Server aborts the soft recovery of EDB file before doing changes to database.
This error may be occurring due to problem in the database or comparison of header information and the log files shows that the removal or replacement of some critical files has been done.
This error will damage your edb file and finally the loss your important data. But you don’t have to worry because you can recover your edb file through software such as Stellar Phoenix Mailbox Exchange Recovery.
Through Exchange Recovery software, you can recover your corrupted or damaged edb files of Microsoft Exchange Server. This software is extremely powerful product to handle edb corruption scenarios. This will repair all your emails, contacts, notes, and it will also recover RTF and HTML messages. This software will restore mailboxes in PST format. Exchange Recovery is very easy to use and also user friendly. One of the best thing in this software is that its support exchange server 5.5, 2000 and 2003 and its compatible with Windows 2000, XP and 2003.
EDB Corruption and Access Problems in Exchange Server
“Access denied to database Mailbox Store (SERVER2K3).
WARNING: “\\SERVER2K3\Microsoft Information Store\First Storage Group\Mailbox Store (SERVER2K3)” is a corrupt file.
This file cannot verify.
Database or database element is corrupt”
In this case, its mean you lost your important data. The error message may occur due to one of the following reason:
1. You don’t have required permissions to access the database
2. Some of important Exchange Server files such as user permissions file go missing
3. Exchange Server database is corrupt and data can not be accessed from it
If you want to fix this problem, then you have only three options:
1. You have appropriate permission from the administrator and then try again.
2. You can repair your Exchange Server.
3. Repair Exchange Server database using Eseutil.exe tool
EDB corruption is one of the most critical situations and should be repaired. Eseutil.exe is an inbuilt Exchange Server utility that can verify and then repair the .edb files. But if you want to fix the errors or edb corruption then you have to go for EDB Recovery
Exchange Recovery Software recovers corrupted or damaged edb files of Microsoft Exchange Server. Stellar Phoenix Mailbox Exchange Server can recover all your emails, notes, contacts, journal, calendar entries and many other things from the corrupted edb files.
One of the best things in this software is that it supports Exchange Server5.5, 2000, and 2003. EDB recovery software is very user friendly and easy to use. Phoenix EDB Recovery software is compatible with Windows XP, 2003 and 2000.
EDB Corruption After Upgrading to Exchange Server 2000 SP3 or Later
Sometimes, when you attempt to mount the Exchange Server database (EDB file), you might come across any of the following events in the Application Event Log of Exchange Server:
Event Type: Error
Event Source: ESE
Event Category: General
Event ID: 505
Description: Information Store (2028) An attempt to open the compressed file “drive:\Exchsrvr\MDBDATA\priv1.edb” for read / write access failed because it could not be converted to a normal file. The open file operation will fail with error -4005 (0xfffff05b). To prevent this error in the future you can manually decompress the file and change the compression state of the containing folder to uncompressed. Writing to this file when it is compressed is not supported.
Or
Event Type: Error
Event Source: MSExchangeIS
Event Category: General
Event ID: 9519
Description: Error 0xfffff05b starting database “First Storage Group\Mailbox Store (EXCHANGE)” on the Microsoft Exchange Information Store. Failed to attach to Jet DB.
This issue generally occurs when you upgrade to Exchange Server 2000 Service Pack 3 or later and the Information Store database is compressed using NTFS (New Technology File System) file system compression. Under some situations, NTFS compression may damage the Exchange Server database like when the EDB file exceeds 4 GB size. In such cases, Exchange Repair is required to work around the issue.
Exchange Server 2000 Service Pack 3 and later do not allow NTFS compressed information store to mount. The files are managed by Extensible Storage Engine (ESE) that needs sector independence for log-based recovery that is not allowed in compression.
This entire behavior of Exchange Server corrupts the EDB file and you are required to repair and restore is using Exchange Recovery software to access your critical data. These software can recover all of the Exchange Server database objects.
Stellar Phoenix Mailbox Exchange Recovery is the most advanced Exchange Repair software that works in most of EDB corruption cases. It works well with Exchange Server 2003, 2000 and 5.5. This software is compatible with Microsoft Windows 2003, XP and 2000
Exchange Database Doesn’t Mount After Installing SP3 or Later to Exchange 2000
In some of the cases, user may fail to mount the information store database and encounter an event in the application log of Event Viewer:
Event Type: Error
Event Source: ESE
Event Category: General
Event ID: 505
Description: Information Store (2028) An attempt to open the compressed file “drive:\Exchsrvr\MDBDATA\priv1.edb” for read / write access failed because it could not be converted to a normal file. The open file operation will fail with error -4005 (0xfffff05b). To prevent this error in the future you can manually decompress the file and change the compression state of the containing folder to uncompressed. Writing to this file when it is compressed is not supported.
Or
Event Type: Error
Event Source: MSExchangeIS
Event Category: General
Event ID: 9519
Description: Error 0xfffff05b starting database “First Storage Group\Mailbox Store (EXCHANGE)” on the Microsoft Exchange Information Store. Failed to attach to Jet DB.
This problem is specifically encountered when user upgrades to Exchange Server SP3 or later. If the information store database has been compressed using NTFS file system compression.
Note: NTFS compression can corrupt Exchange database under critical situations like when the information store reaches to about 4 GB in size, in which Exchange Server Recovery is required.
Exchange Server SP3 and later versions, including Exchange Server 2003 don’t allow NTFS compressed information store to mount. These files are managed by ESE (Extensible Storage Engine) which require sector independence for log-based recovery process, which is not allowed in compressed files. Thus database corruption may result, specifically in database files, larger than 128 MB, which require Exchange Server Repair. Files, smaller than 128 MB, are automatically decompressed in Exchange Server SP3 and later.
In order to resolve the issue, we need to decompress the folders of Information store databases and logs after dismounting the database. Then, we need to carry out offline defragmentation using eseutil /d command and mount the database again. If the database comes out to be corrupt, we need to apply Exchange Server Repair or else perform the online backup of the database.
Exchange Server Recovery can be performed using Eseutil utility, but the corrupt pages will be deleted. So using commercial Exchange Server Repair software can be used which apply powerful, yet safe, scanning algorithms to repair the corrupt database.
Stellar Phoenix Mailbox Exchange Recovery is an excellent Exchange Sever Recovery software which is compatible with Exchange Server 5.5, 2000 and 2003. This Exchange Server Repair software has interactive interface and recover mailxes in PST format, usable with MS Outlook.
EDB Recovery after Corruption to the Database Elements
Sometimes when you attempt to create backup of Microsoft Exchange Server database, which is damaged and inaccessible, you might come across the below given error message:
“Database or database element is corrupt”
Furthermore, with this error message, you might also get a statement, which states that this file can not be verified. Due to corruption, the Exchange Server can not recognize the database and thus can not access it. At this point, you need to identify the cause of data loss and carry out Exchange Server Repair by sorting it out.
Root of the issue
As stated in the above error message, this situation occurs due to corruption to the EDB file. The corruption could be the possible result to virus infection, accidental system shutdown, application errors, operating system malfunction and other similar reasons.
Resolution
In order to fix this issue, you should go for Eseutil/p utility. This is an inbuilt tool in Microsoft Exchange Server that is used to repair damaged EDB file. This tool scans the damaged database and can repair in a number of cases.
Although, this utility is helpful in resolving this error message, but it also has a downside. It deletes all of the database elements that are not recognized by this tool. This behavior of Eseutil tool cause critical data loss situations and make your data permanently inaccessible. To safely retrieve your critical data, go for advanced and powerful Exchange Server Recovery software.
These software are particularly designed to safely, smoothly and thoroughly scan entire database and retrieve all of the inaccessible database objects. These software use efficient and powerful scanning algorithms to achieve perfect Exchange Server Repair. With interactive and simple graphical user interface, such applications are easy to use and do not require sound and prior technical skills.
Stellar Phoenix Mailbox Exchange Recovery is the most advanced and effective software that can handle all EDB corruption scenarios. It can repair and restore damaged EDB file of Exchange Server 2003, 2000 and 5.5. This software is compatible with Windows 2003, XP and 2000.
Sunday, May 31, 2009
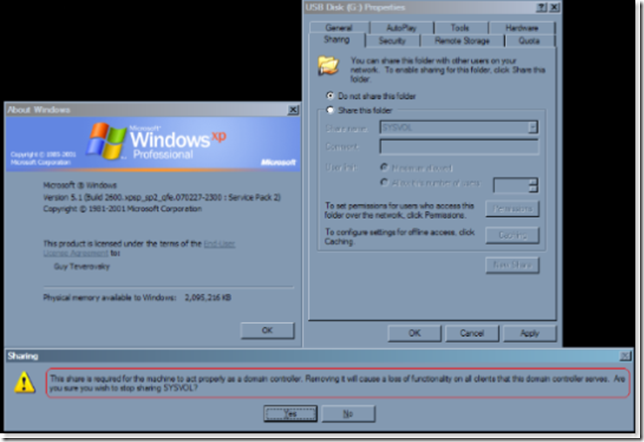
XP as Domain Controller
This is very funny XP machine as a domain controller
1) Create a share called SYSVOL on an XP machine
2) Try to unshare the directory you shared as SYSVOL.
3) You will get a nice warning stating:
"This share is required for the machine to act properly as a domain controller. Removing it will cause a loss of functionality on all clients that this domain controller serves. Are you sure you wish to stop sharing SYSVOL?"
But do not worry - unsharing SYSVOL on XP will not break your AD. This is just an example of code reuse that Microsoft does.
PowerGUI, a graphical user interface and script editor for Windows PowerShell!
What is PowerGUI?
PowerGUI is an extensible graphical administrative console for managing systems based on Windows PowerShell. These include Windows OS (XP, 2003, Vista), Exchange 2007, Operations Manager 2007 and other new systems from Microsoft. The tool allows to use the rich capabilities of Windows PowerShell in a familiar and intuitive GUI console.
PowerShell is built-in feature under Windows Server 2008
Download PowerShell for Windows Vista, Windows 2003 and Windows XP
http://www.microsoft.com/windowsserver2003/technologies/management/powershell/download.mspx
Power Packs
Active Directory: http://powergui.org/kbcategory.jspa?categoryID=46
Microsoft Operations Manager (MOM): http://powergui.org/kbcategory.jspa?categoryID=49
Virtualization: http://powergui.org/kbcategory.jspa?categoryID=290
Microsoft Exchange: http://powergui.org/kbcategory.jspa?categoryID=47
Network: http://powergui.org/kbcategory.jspa?categoryID=48
SQL: http://powergui.org/kbcategory.jspa?categoryID=54
Others: http://powergui.org/kbcategory.jspa?categoryID=21
User manuals
For PowerGUI and QAD cmdlets user manuals and FAQ please visit PowerGUI wiki.
Blogs
Latest PowerGUI and QAD cmdlets news can be found at our team members' blogs:
- Dmitry's PowerBlog by Dmitry Sotnikov
- Poshoholic.com by Kirk Munro
Videos and Flash Demos
- Interactive Walkthrough - Take a guided tour of PowerGUI as we perform some basic tasks in both the user interface and the script editor.
- Introduction to PowerGUI demo - this is the most basic and introductory demo using Exchange 2007 environment to show how PowerGUI can be used to manage mailboxes, produce reports, how the console can be extended, and finally how these extensions are shared with other community members.
- How to Create a PowerPack - this demonstrates how to add nodes, links and actions to PowerGUI and how you can share your nodes, links and actions with the community as a PowerPack.
- Extending PowerGUI - this is an advanced demo on how PowerGUI works and how it can be extended with simple and script nodes/links/actions and how you can use .NET, WMI, and ADSI when PowerShell is not enough.
- Introduction to the Hyper-V PowerPack - Kirk Munro (the Poshoholic) provides an introduction to the Hyper-V PowerPack that he created.
- Managing Operations Manager 2007 with PowerGUI - Rob "Deuce" Doucette is demoing his PowerPack for OpsManager 2007 (also known as MOM).
- Advanced Exchange 2007 Management - mailbox provisioning, certificate management, public folder management - all through PowerGUI UI.
- Automated Software Testing - test your software projects with PowerShell and PowerGUI.
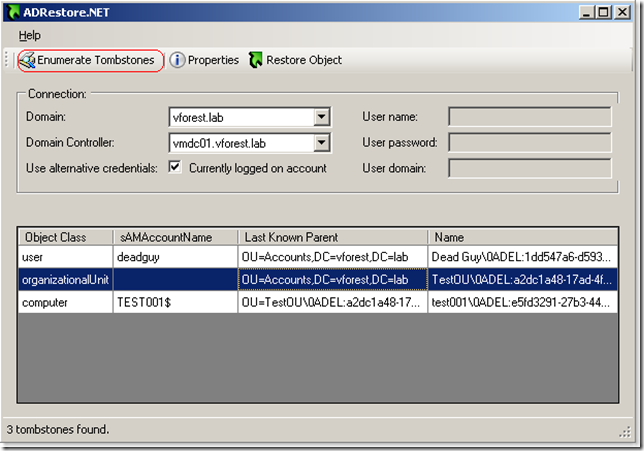
ADRestore GUI version
Accidentally deleted user, computer account or OU’s from Active Directory. Don’t worry, now you can get them back using ADRestore tool using GUI interface.
Though there is a command line version of tombstone reanimation tool called adrestore - sysinternals, many people are not CLI savvies and having a GUI version of this functionality could really help them out.
Insight on tombstone: Reanimating Active Directory Tombstone Objects - By Gil Kirkpatrick
Gil Kirkpatrick's article at Technet
Main features:
- Browsing the tombstones
- Domain Controller targeting
- Can be used with alternative credentials (convenient if you do not logon to your desktop as Domain Admin, which you should never do anyway)
- User/Computer/OU/Container reanimation
- Preview of tombstone attributes
Here are some sceenshots:
Previewing the tombstone attributes 
Restoring a deleted user account 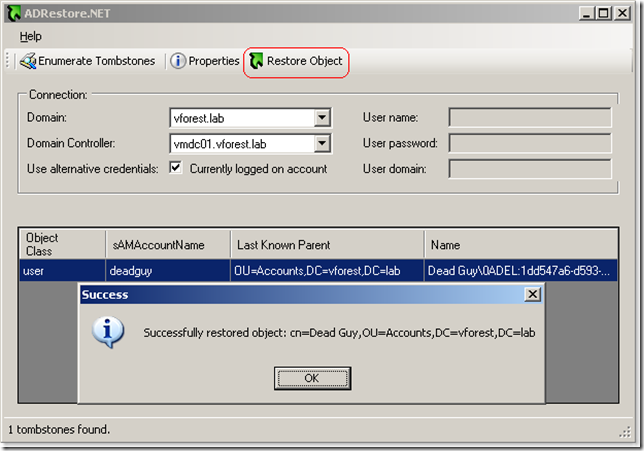
Notice that if you delete an OU with accounts in it, you will have to restore first the OUs the accounts were in, otherwise the reanimation of the child object will fail. It is not enough to create an OU with the same name as this will be a totally new object in AD and child object's lastKnowParent attribute will still reference the deleted OU. Here is a walthrough:
TestOU organizational unit is deleted: 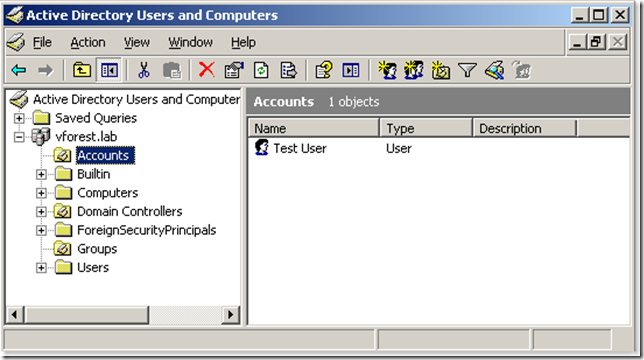
State of tombstones (notice that lastKnownParent attribute of user and computer accounts reference the deleted OU): 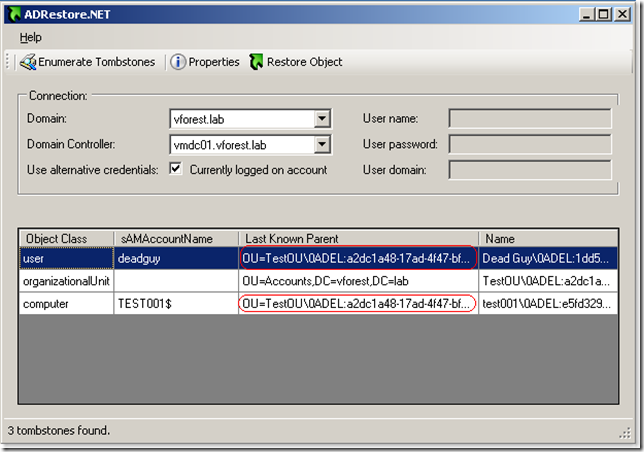
OU is restored (lastKnowParent points to the restored OU's distinguished name): 
Both computer and user accounts that resided in TestOU are reanimated: 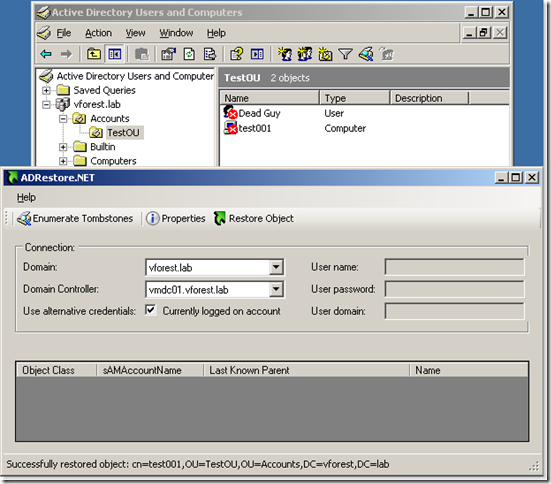
Download ADRestore.NET
Failover Clustering Windows 2008 Videos by John Savill
- Creating Windows Server 2008 Failover Clusters:
http://www.savilltech.com/Videos/clustercreate/ClusterCreate.wmv - Configuring a Windows Server 2008 Failover Cluster from the command line: http://www.savilltech.com/Videos/clustercmd/clustercmd.wmv
- Understanding Failover Cluster Quorum:
http://www.savilltech.com/Videos/ClusterQuorum/ClusterQuorum.wmv - Hyper-V Quick Migration:
http://www.savilltech.com/Videos/QuickMigration/QuickMigration.wmv - Configuring iSCSI connections from the command line:
http://www.savilltech.com/Videos/iscsicli/iscsicli.wmv - Failover Clustering with MELIO File System:
http://www.savilltech.com/Videos/meliofs/meliofs.wmv
Performance Analysis of Logs (PAL) Tool
Tired of parsing the Perfmon (*.blg) manually. Let PAL make your job easier, give you html output and highlight high thresholds.
Website: http://www.codeplex.com/PAL
Project Description
Ever have a performance problem, but don't know what performance counters to collect or how to analyze them? The PAL (Performance Analysis of Logs) tool is a new and powerful tool that reads in a performance monitor counter log (any known format) and analyzes it using complex, but known thresholds (provided). The tool generates an HTML based report which graphically charts important performance counters and throws alerts when thresholds are exceeded. The thresholds are originally based on thresholds defined by the Microsoft product teams and members of Microsoft support, but continue to be expanded by this ongoing project. This tool is not a replacement of traditional performance analysis, but it automates the analysis of performance counter logs enough to save you time. This is a VBScript and requires Microsoft LogParser (free download).
Features
- Thresholds files for most of the major Microsoft products such as IIS, MOSS, SQL Server, BizTalk, Exchange, and Active Directory.
- An easy to use GUI interface which makes creating batch files for the PAL.vbs script.
- A GUI editor for creating or editing your own threshold files.
- Creates an HTML based report for ease of copy/pasting into other applications.
- Analyzes performance counter logs for thresholds using thresholds that change their critieria based on the computer's role or hardware specs.
Download Link: http://www.codeplex.com/PAL/Release/ProjectReleases.aspx?ReleaseId=16807
To use PAL
The PAL tool is primarily a VBScript that requires arguments/parameters passed to it in order to properly analyze performance monitor logs. In v1.1 and later of PAL, a GUI interface has been added to help with this process.Requirements
Operating Systems
PAL runs successfully on all of the following operating systems: Windows XP SP2, Windows Vista, and Windows 2003 Server. 32-bit only due to OWC11 requirements.
Note: The optional GUI (windows form) portion of PAL requires the Microsoft .NET Framework v2.0.
Log Parser 2.2
Log parser is a powerful, versatile tool that provides universal query access to text-based data such as log files, XML files and CSV files, as well as key data sources on the Windows® operating system such as the Event Log, the Registry, the file system, and Active Directory®. PAL uses the Log Parser tool to query perform logs and to create charts and graphs for the PAL report.
http://www.microsoft.com/downloads/details.aspx?FamilyID=890cd06b-abf8-4c25-91b2-f8d975cf8c07&DisplayLang=en
Microsoft Office Web Components 2003
Log Parser requires the Office Web Components 2003 in order to create charts.
http://www.microsoft.com/downloads/details.aspx?FamilyID=7287252c-402e-4f72-97a5-e0fd290d4b76
Training
Watch online at: http://www.livemeeting.com/cc/microsoft/view?id=JKGT3N
or
Download it (20071005IntrotoPALwmv.zip) from:
https://www.codeplex.com/Release/ProjectReleases.aspx?ProjectName=PAL&ReleaseId=6759
Related Blogs and Reviews
Clint Huffman's Windows Performance Analysis Blog
http://blogs.technet.com/clint_huffman
Mike Lagase's Exchange Performance Analysis Blog
http://blogs.technet.com/mikelag/archive/2008/08/20/performance-troubleshooting-using-the-pal-tool.aspx
Two Exchange Server Tools You Should Know About
http://windowsitpro.com/article/articleid/100132/two-exchange-server-tools-you-should-know-about.html
Few useful Debugging Commands - WinDbg
All of these commands are for kernel mode. These are few useful commands, that I use on daily basis for debugging. I hope you find them useful
Vertarget:
Lists Version information for the machine/dump you're debugging. You can also use "version" to tell you about the debugger bits.
1: kd> vertarget
Windows Kernel Version 6001 (Service Pack 1) MP (4 procs) Free x64
Product: LanManNt, suite: TerminalServer SingleUserTS
Built by: 6001.18000.amd64fre.longhorn_rtm.080118-1840
Kernel base = 0xfffff800`0160c000 PsLoadedModuleList = 0xfffff800`017d1db0
Debug session time: Tue Apr 1 14:29:22.553 2008 (GMT-7)
System Uptime: 0 days 0:03:14.328
!sysinfo
Good utility to check the CPU revs, BIOS revs, etc
1: kd> !sysinfo machineid
Machine ID Information [From Smbios 2.31, DMIVersion 0, Size=1695]
BiosVendor = Phoenix Technologies LTD
BiosVersion = 6.00
BiosReleaseDate = 09/24/2007
SystemManufacturer = VMware, Inc.
SystemProductName = VMware Virtual Platform
SystemVersion = None
BaseBoardManufacturer = Intel Corporation
BaseBoardProduct = 440BX Desktop Reference Platform
BaseBoardVersion = None
1: kd> !sysinfo cpuinfo
[CPU Information]
~MHz = REG_DWORD 2000
Component Information = REG_BINARY 0,0,0,0,0,0,0,0,0,0,0,0,1,0,0,0
Configuration Data = REG_FULL_RESOURCE_DESCRIPTOR ff,ff,ff,ff,ff,ff,ff,ff,0,0,0,0,0,0,0,0
Identifier = REG_SZ x86 Family 6 Model 15 Stepping 8
ProcessorNameString = REG_SZ Intel(R) Xeon(R) CPU L5335 @ 2.00GHz
Update Signature = REG_BINARY 0,0,0,0,b4,0,0,0
Update Status = REG_DWORD 2
VendorIdentifier = REG_SZ GenuineIntel
MSR8B = REG_QWORD b400000000
Getting the Server Name from the dump:
It's quite a bit easier to do internally, but this will get it done too. Good to know you're debugging the right server. :)
1: kd> dS srv!srvcomputername
e1b64db0 "Phantom"
!thread
Display current thread on the target system
1: kd> !thread
THREAD fa6046c8 Cid 1ab4.1f34 Teb: 00000000 Win32Thread: 00000000 RUNNING on processor 1
IRP List:
fa0cc490: (0006,01d8) Flags: 00000404 Mdl: 00000000
Not impersonating
Owning Process fa15f3e0 Image: cmd.exe
Wait Start TickCount 16627733 Ticks: 0
Context Switch Count 1102 LargeStack
UserTime 00:00:00.312
KernelTime 00:00:00.109
Win32 Start Address 0x00407ccc
Start Address 0x77e617f8
Stack Init f1e9d000 Current f1e9c4b8 Base f1e9d000 Limit f1e99000 Call 0
Priority 6 BasePriority 6 PriorityDecrement 0
ChildEBP RetAddr Args to Child
f1e9c174 e105bba7 0000008e c0000005 e11294a0 nt!KeBugCheckEx+0x1b (FPO: [Non-Fpo])
f1e9c538 e10346b4 f1e9c554 00000000 f1e9c5a8 nt!KiDispatchException+0x3a2 (FPO: [Non-Fpo])
f1e9c5a0 e1034668 f1e9c628 e11294a0 badb0d00 nt!CommonDispatchException+0x4a (FPO: [0,20,0])
f1e9c628 e1131ac4 fa6046c8 fa15f3e0 f9de0310 nt!Kei386EoiHelper+0x186
f1e9c628 e1131ac4 fa6046c8 fa15f3e0 f9de0310 nt!SeCreateAccessState+0x27 (FPO: [Non-Fpo])
f1e9c648 e112d742 f9de0310 f9de03c8 00000180 nt!SeCreateAccessState+0x27 (FPO: [Non-Fpo])
f1e9c680 e112c65d 00000000 00000000 b57f0000 nt!ObOpenObjectByName+0x8f (FPO: [Non-Fpo])
f1e9c6fc e1131d22 f1e9c7fc 00000180 f1e9c7b8 nt!IopCreateFile+0x447 (FPO: [Non-Fpo])
f1e9c758 f4df068a f1e9c7fc 00000180 f1e9c7b8 nt!IoCreateFile+0xa3 (FPO: [Non-Fpo])
WARNING: Stack unwind information not available. Following frames may be wrong.
f1e9c7a4 f4defe67 80005510 00540052 e9fa0920 savrt+0x4668a
00000000 00000000 00000000 00000000 00000000 savrt+0x45e67
!irp
Display information about an I/O request packet
1: kd> !irp fa0cc490
Irp is active with 10 stacks 12 is current (= 0xfa0cc68c)
No Mdl: No System Buffer: Thread fa6046c8: Irp is completed.
cmd flg cl Device File Completion-Context
[ 0, 0] 0 0 00000000 00000000 00000000-00000000
Args: 00000000 00000000 00000000 00000000
[ 0, 0] 0 0 00000000 00000000 00000000-00000000
Args: 00000000 00000000 00000000 00000000
[ 12, 0] 0 0 fd1a8020 00000000 00000000-00000000
\FileSystem\Ntfs
Args: 00000000 00000000 00000000 00000000
[ 12, 0] 0 0 fd101cd8 00000000 00000000-00000000
*** ERROR: Symbol file could not be found. Defaulted to export symbols for SYMEVENT.SYS -
\Driver\SymEvent
Args: 00000000 00000000 00000000 00000000
!poolused
Investigate what data structures are consuming the various memory pools
!poolused 2 - sorted by Non-paged pool, summary
!poolused 3 - sorted by Non-Paged pool, details*
!poolused 4 - sorted by Paged pool, summary
!poolused 5 - sorted by Paged pool, details*
!running -ti
This will dump the stacks of each thread that is running on each processor
1: kd> !running -ti
System Processors 3 (affinity mask)
Idle Processors 1
Prcb Current Next
0 ffdff120 8089d8c0 ................
ChildEBP RetAddr
f45f0c70 bf8bb568 win32k!CanForceForeground+0x42
f45f0ca4 bf8bab6a win32k!CheckAllowForeground+0x79
f45f0cb4 bf8b7f41 win32k!xxxInitProcessInfo+0x54
f45f0cdc bf8b8032 win32k!xxxUserProcessCallout+0x23
f45f0cf8 809456dd win32k!W32pProcessCallout+0x43
f45f0d54 8088948e nt!PsConvertToGuiThread+0x13d
f45f0d58 00000000 nt!KiBBTUnexpectedRange+0xc
WARNING: Process directory table base EFFC7BE0 doesn't match CR3 EFFC7020
WARNING: Process directory table base EFFC7BE0 doesn't match CR3 EFFC7020
1 f7727120 8c034bd0 ................
*** Stack trace for last set context - .thread/.cxr resets it
ChildEBP RetAddr
f45f0c70 bf8bb568 win32k!CanForceForeground+0x42
f45f0ca4 bf8bab6a win32k!CheckAllowForeground+0x79
f45f0cb4 bf8b7f41 win32k!xxxInitProcessInfo+0x54
f45f0cdc bf8b8032 win32k!xxxUserProcessCallout+0x23
f45f0cf8 809456dd win32k!W32pProcessCallout+0x43
f45f0d54 8088948e nt!PsConvertToGuiThread+0x13d
f45f0d58 00000000 nt!KiBBTUnexpectedRange+0xc
!stacks
This is a great utility to check what threads are waiting on for each process. Find out more in the debuggers chm.
1: kd> !stacks 2
Proc.Thread .Thread Ticks ThreadState Blocker
Max cache size is : 1048576 bytes (0x400 KB)
Total memory in cache : 0 bytes (0 KB)
Number of regions cached: 0
0 full reads broken into 0 partial reads
counts: 0 cached/0 uncached, 0.00% cached
bytes : 0 cached/0 uncached, 0.00% cached
** Prototype PTEs are implicitly decoded
[fffffa8000c77950 System]
4.000008 fffffa8000c774c0 ffffe94b GATEWAIT nt!KiSwapContext+0x7f
nt!KiSwapThread+0x2fa
nt!KeWaitForGate+0x22a
nt!MmZeroPageThread+0x162
nt!Phase1Initialization+0xe
nt!PspSystemThreadStartup+0x57
nt!KiStartSystemThread+0x16
4.000010 fffffa8000ca0720 ffffff8c Blocked nt!KiSwapContext+0x7f
nt!KiSwapThread+0x2fa
nt!KeWaitForSingleObject+0x2da
nt!PopIrpWorkerControl+0x22
nt!PspSystemThreadStartup+0x57
nt!KiStartSystemThread+0x16
4.000014 fffffa8000c78bb0 fffffcb0 Blocked nt!KiSwapContext+0x7f
nt!KiSwapThread+0x2fa
nt!KeWaitForSingleObject+0x2da
nt!PopIrpWorker+0x164
nt!PspSystemThreadStartup+0x57
nt!KiStartSystemThread+0x16
!locks
It will display a list of all kernel mode locks that are being held by threads. Each lock is displayed with the mode the lock was taken out with (shared or exclusive). The owning thread(s) will be listed with an asterisk next to the thread id. If any waiters are queued up for the lock, it will list these too.
1: kd> !locks
**** DUMP OF ALL RESOURCE OBJECTS ****
KD: Scanning for held locks....
Resource @ nt!CmpRegistryLock (0xe10ad4c0) Shared 2 owning threads
Contention Count = 87
Threads: fc783020-01<*> feee9db0-01<*>
KD: Scanning for held locks...
Resource @ 0xfeeed078 Shared 4 owning threads
Threads: fad42330-01<*> fad33020-01<*> fad33db0-01<*> fad42b40-01<*>
KD: Scanning for held locks.......................................
Resource @ 0xfc6df828 Shared 1 owning threads
Threads: fa6046c8-01<*>
KD: Scanning for held locks..
Resource @ 0xfc7e91c8 Shared 1 owning threads
Threads: fa6046c8-01<*>
KD: Scanning for held locks.
Resource @ savrt (0xf4daf040) Shared 1 owning threads
Contention Count = 1
Threads: fa6046c8-01<*>
KD: Scanning for held locks.........................
Resource @ 0xfa6c1380 Shared 1 owning threads
Contention Count = 71388
Threads: f9ed1918-01<*>
KD: Scanning for held locks..............................
Resource @ 0xfaab7840 Shared 1 owning threads
Threads: feee9db3-01<*> *** Actual Thread feee9db0
KD: Scanning for held locks....................
11756 total locks, 7 locks currently held
!qlocks
command which displays all the various spinlocks. All processors are displayed across the top and codes appear next to the corresponding spinlock if owned or not, waiting or corrupt.
1: kd> !qlocks
Key: O = Owner, 1-n = Wait order, blank = not owned/waiting, C = Corrupt
Processor Number
Lock Name 0 1 2 3
KE - Dispatcher
MM - Expansion
MM - PFN
MM - System Space
CC - Vacb
CC - Master
EX - NonPagedPool
IO - Cancel
EX - WorkQueue
IO - Vpb
IO - Database
IO - Completion
NTFS - Struct
AFD - WorkQueue
CC - Bcb
MM - NonPagedPool
!PCR
Command will show you some useful info from the processor control block. Like the current thread, next, DPQ queues (Can run !dpcs).
1: kd> !pcr
KPCR for Processor 1 at f7727000:
Major 1 Minor 1
NtTib.ExceptionList: f4ac3d44
NtTib.StackBase: 00000000
NtTib.StackLimit: 00000000
NtTib.SubSystemTib: f7727fe0
NtTib.Version: 00336d13
NtTib.UserPointer: 00000002
NtTib.SelfTib: 7ffde000
SelfPcr: f7727000
Prcb: f7727120
Irql: 0000001f
IRR: 00000000
IDR: ffffffff
InterruptMode: 00000000
IDT: f772d800
GDT: f772d400
TSS: f7727fe0
CurrentThread: 8c034bd0
NextThread: 00000000
IdleThread: f772a090
DpcQueue:
lm t n
Displaying the list of installed drivers reveals our obsolete culprit
1: kd> lm t n
start end module name
dd800000 dd9d0000 win32k win32k.sys Wed Mar 19 17:01:40 2008 (47E0F99C)
dd9d0000 dd9e7000 dxg dxg.sys Sat Feb 17 11:44:39 2007 (45D69D4F)
dd9e7000 dda3e100 ati2drad ati2drad.dll Mon Mar 22 21:53:41 2004 (405F130D)
dda3f000 dda5d000 RDPDD RDPDD.dll Sat Feb 17 19:31:19 2007 (45D70AAF)
e1000000 e127a000 nt ntkrnlmp.exe Mon Mar 05 18:32:02 2007 (45EC14CA)
e127a000 e12a6000 hal halmacpi.dll Sat Feb 17 11:18:26 2007 (45D6972A)
f1ca4000 f1cb81e0 naveng naveng.sys Fri Aug 15 09:30:26 2008 (48A4FF5A)
f1cb9000 f1d8ca20 navex15 navex15.sys Fri Aug 15 08:40:42 2008 (48A4F3B2)
f31a0000 f31cb000 RDPWD RDPWD.SYS Sat Feb 17 11:14:38 2007 (45D69646)
f38b4000 f38bf000 TDTCP TDTCP.SYS Sat Feb 17 11:14:32 2007 (45D69640)
f3904000 f3912000 HIDCLASS HIDCLASS.SYS Tue Mar 25 12:40:17 2003 (3E8000D9)
f3d14000 f3d1d000 hidusb hidusb.sys Tue Mar 25 12:40:17 2003 (3E8000D9)
f3d74000 f3d9e000 Fastfat Fastfat.SYS Sat Feb 17 11:57:55 2007 (45D6A06B)
f4046000 f40a3000 srv srv.sys Sat Feb 17 11:57:20 2007 (45D6A048)
f466b000 f4683000 clusnet clusnet.sys Sat Feb 17 11:32:57 2007 (45D69A91)
f48b3000 f48c8000 Cdfs Cdfs.SYS Sat Feb 17 11:57:08 2007 (45D6A03C)
!LMI
When I want to find out ifno about a particular driver in the dump, i use "lm n t" to get all of them, but then !lmi to drill into one.
1: kd> !lmi win32k.sys
Loaded Module Info: [win32k.sys]
Module: win32k
Base Address: bf800000
Image Name: win32k.sys
Machine Type: 332 (I386)
Time Stamp: 47e0f99c Wed Mar 19 17:01:40 2008
Size: 1d0000
CheckSum: 1cd134
Characteristics: 10e perf
Debug Data Dirs: Type Size VA Pointer
CODEVIEW 23, 1935ac, 1929ac RSDS - GUID: {09B6D936-14C4-4CA1-90CF-A00888CD89A8}
Age: 2, Pdb: win32k.pdb
CLSID 4, 1935a8, 1929a8 [Data not mapped]
Image Type: MEMORY - Image read successfully from loaded memory.
Symbol Type: PDB - Symbols loaded successfully from symbol server.
c:\symcache\win32k.pdb\09B6D93614C44CA190CFA00888CD89A82\win32k.pdb
Load Report: public symbols , not source indexed
c:\symcache\win32k.pdb\09B6D93614C44CA190CFA00888CD89A82\win32k.pdb
Wednesday, May 27, 2009
Installing Secondary DNS,
 Reduced: 80% of original size [ 638 x 479 ] - Click to view full image
Reduced: 80% of original size [ 638 x 479 ] - Click to view full image
Right Click the "Forward Look-up Zone" then Select "New Zone"
 Reduced: 80% of original size [ 636 x 480 ] - Click to view full image
Reduced: 80% of original size [ 636 x 480 ] - Click to view full image
Click "Next"
 Reduced: 80% of original size [ 637 x 480 ] - Click to view full image
Reduced: 80% of original size [ 637 x 480 ] - Click to view full image
Select "one or more DNS are running on this network" then enter your Primary DNS ip address and Click "next"
 Reduced: 80% of original size [ 636 x 478 ] - Click to view full image
Reduced: 80% of original size [ 636 x 478 ] - Click to view full image
Select "yes, create a forward lookup zone" and Click "Next"
 Reduced: 80% of original size [ 638 x 484 ] - Click to view full image
Reduced: 80% of original size [ 638 x 484 ] - Click to view full image
Select "Secondary DNS" and click "Next"
 Reduced: 80% of original size [ 635 x 477 ] - Click to view full image
Reduced: 80% of original size [ 635 x 477 ] - Click to view full image
Type the name in zone "e.g, secondary.nanflexaltech.com" and click "Next"
 Reduced: 80% of original size [ 639 x 479 ] - Click to view full image
Reduced: 80% of original size [ 639 x 479 ] - Click to view full image
Enter your Primary DNS ip address and "Add" then Click "Next"
 Reduced: 80% of original size [ 634 x 478 ] - Click to view full image
Reduced: 80% of original size [ 634 x 478 ] - Click to view full image
Select "No, Donot create reverse lookup zone" and click "Next"
 Reduced: 80% of original size [ 637 x 478 ] - Click to view full image
Reduced: 80% of original size [ 637 x 478 ] - Click to view full image
Click "Finish" and you will see the picture below, if anything went good, you will see your secondary DNS up and running
 Reduced: 80% of original size [ 638 x 452 ] - Click to view full image
Reduced: 80% of original size [ 638 x 452 ] - Click to view full image
Installing Active Directory - Secondary Domain, Secondary Domain Controller in Windows 2000 Server
Active Directory was previewed in 1996, released first with Windows 2000 Server edition, and revised to extend functionality and improve administration in Windows Server 2003. Additional improvements were made in both Windows Server 2003 R2 and Windows Server 2008.
Installing Active Directory (Secondary Domain Controller)
 Reduced: 80% of original size [ 636 x 479 ] - Click to view full image
Reduced: 80% of original size [ 636 x 479 ] - Click to view full image
click "Start menu" and choose "Run" and enter "dcpromo" and click "Ok"
 Reduced: 80% of original size [ 638 x 478 ] - Click to view full image
Reduced: 80% of original size [ 638 x 478 ] - Click to view full image
click "Next"
 Reduced: 80% of original size [ 636 x 478 ] - Click to view full image
Reduced: 80% of original size [ 636 x 478 ] - Click to view full image
Select "Secondary domain controller for an existing domain" and click "Next"
 Reduced: 80% of original size [ 639 x 478 ] - Click to view full image
Reduced: 80% of original size [ 639 x 478 ] - Click to view full image
Enter your network credential and click "Next"
 Reduced: 79% of original size [ 641 x 477 ] - Click to view full image
Reduced: 79% of original size [ 641 x 477 ] - Click to view full image
Type your Existing Domain (e.g: NANFLEXALTECH)
 Reduced: 79% of original size [ 641 x 476 ] - Click to view full image
Reduced: 79% of original size [ 641 x 476 ] - Click to view full image
small pop-up will appear and click "Yes" and click "Next"
 Reduced: 80% of original size [ 638 x 479 ] - Click to view full image
Reduced: 80% of original size [ 638 x 479 ] - Click to view full image
click "Next"
 Reduced: 80% of original size [ 639 x 481 ] - Click to view full image
Reduced: 80% of original size [ 639 x 481 ] - Click to view full image
click "Next"
 Reduced: 80% of original size [ 636 x 477 ] - Click to view full image
Reduced: 80% of original size [ 636 x 477 ] - Click to view full image
Create your "Directory services restore mode administrator password" and click "Next"
 Reduced: 80% of original size [ 637 x 477 ] - Click to view full image
Reduced: 80% of original size [ 637 x 477 ] - Click to view full image
click "Next" and you will see the picture below
 Reduced: 80% of original size [ 639 x 455 ] - Click to view full image
Reduced: 80% of original size [ 639 x 455 ] - Click to view full image
 Reduced: 80% of original size [ 637 x 458 ] - Click to view full image
Reduced: 80% of original size [ 637 x 458 ] - Click to view full image
click "Finish"
 Reduced: 80% of original size [ 635 x 458 ] - Click to view full image
Reduced: 80% of original size [ 635 x 458 ] - Click to view full image
click "Restart Now"
 Reduced: 80% of original size [ 639 x 479 ] - Click to view full image
Reduced: 80% of original size [ 639 x 479 ] - Click to view full image
If everything went good, you will see the above picture when you run your "Active Directory User and Computer"
DISCLAIMER
WE USE LINKS TO SITES AND NOT DIRECT DOWNLOAD LINKS. THERE NO FILES HOSTED ON OUR SERVER,THEY ARE ONLY INDEXED MUCH LIKE GOOGLEWORKS.The hosting server or the administrator cannot be held responsible for the contents of any linked sites or any link contained in a linked site, or changes / updates to such sites.
BY ENTERING THIS SITE YOU AGREE TO BE BOUND BY THESE CONDITIONS
If you don't like the software posted here, please don't hesitate to let us know and we will unpost it.